Release Date: NOV 4, 2020
Build Details
- VMware ESXi (formerly ESX) is an enterprise-class, type-1 hypervisor developed by VMware for deploying and serving virtual computers.As a type-1 hypervisor, ESXi is not a software application that is installed on an operating system (OS); instead, it includes and integrates vital OS components, such as a kernel. After version 4.1 (released in 2010), VMware renamed ESX to ESXi.
- Download the installer for ESXi. See the VMware Web site topic Using MD5 Checksums at http://www.vmware.com/download/md5.html.
- Start your free 30-day trial of Altaro VM Backup for VMware today and see why it's trusted by 50k+ organizations worldwide. Get started now and run your first backup in under 15 mins! The ESXi hypervisor is free to use save for a few catches.
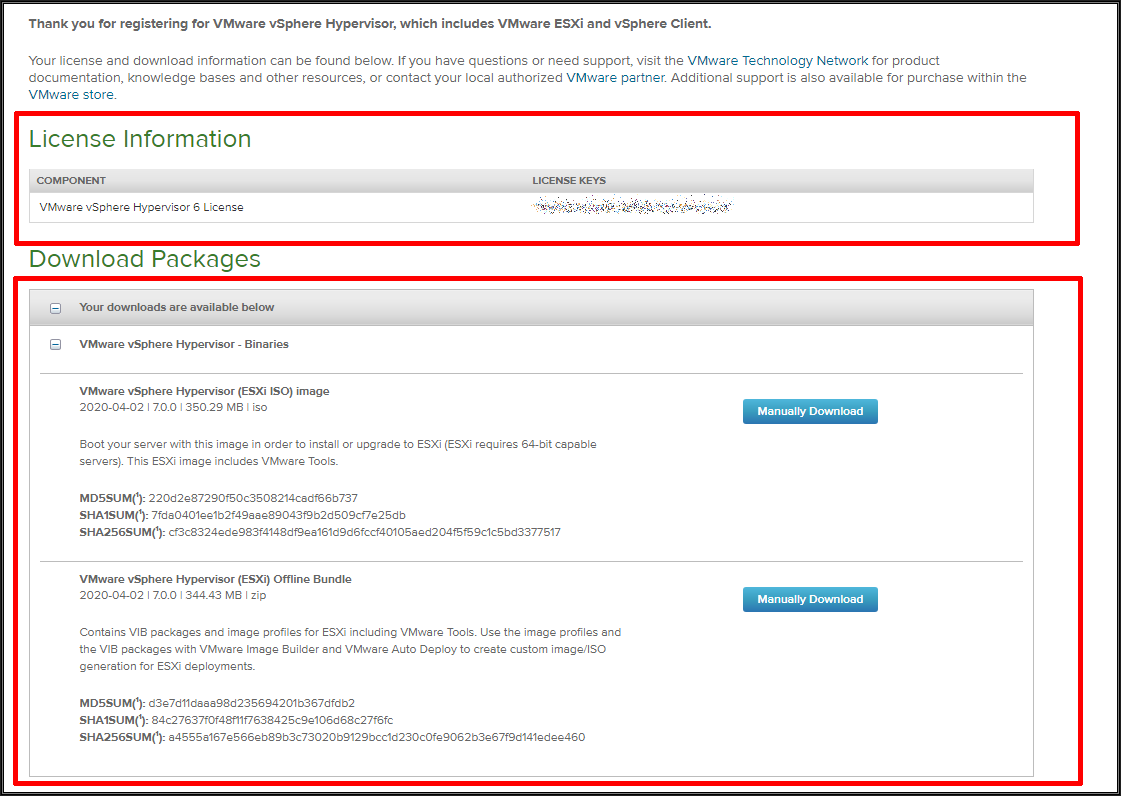
Download the VMware ESXi 6.0 Free Hypervisor installer image along with free license keys. Register or Login with your VMware account credentials Once you have logged in, you will be provided with the option to download the ESXi 6.0 Installation ISO and VMware vSphere client along with the VMware ESXi Free License Keys.
| Download Filename: | ESXi670-202011001.zip |
| Build: | 17098360 |
| Download Size: | 343.1 MB |
| md5sum: | c3923eccb953d091d3cb4fb62f9c5b87 |
| sha1checksum: | 530099e9e69735c06d82ed3a61861a0813da88d3 |
| Host Reboot Required: | Yes |
| Virtual Machine Migration or Shutdown Required: | Yes |
Bulletins
| Bulletin ID | Category | Severity |
| ESXi670-202011301-SG | Security | Critical |
Rollup Bulletin
This rollup bulletin contains the latest VIBs with all the fixes since the initial release of ESXi 6.7.
| Bulletin ID | Category | Severity |
| ESXi670-202011001 | Security | Critical |
Image Profiles
VMware patch and update releases contain general and critical image profiles. Application of the general release image profile applies to new bug fixes.
| Image Profile Name |
| ESXi-6.7.0-20201103001-standard |
| ESXi-6.7.0-20201103001-no-tools |
For more information about the individual bulletins, see the Download Patches page and the Resolved Issues section.
Patch Download and Installation
The typical way to apply patches to ESXi hosts is through the VMware vSphere Update Manager. For details, see the About Installing and Administering VMware vSphere Update Manager.
ESXi hosts can be updated by manually downloading the patch ZIP file from the VMware download page and installing the VIB by using the esxcli software vib command. Additionally, the system can be updated using the image profile and the esxcli software profile command.
For more information, see the vSphere Command-Line Interface Concepts and Examples and the vSphere Upgrade Guide.
Resolved Issues
The resolved issues are grouped as follows.
ESXi670-202011301-SGVsphere Hypervisor
| Patch Category | Security |
| Patch Severity | Critical |
| Host Reboot Required | Yes |
| Virtual Machine Migration or Shutdown Required | Yes |
| Affected Hardware | N/A |
| Affected Software | N/A |
| VIBs Included |
|
| PRs Fixed | N/A |
| CVE numbers | CVE-2020-3992 |
This patch updates the esx-base, esx-tboot, vsan, and vsanhealth VIBs.
Vmware Esxi Free Key
OpenSLP as used in ESXi has a use-after-free issue. This issue might allow a malicious actor with network access to port 427 on an ESXi host to trigger a use-after-free in the OpenSLP service resulting in remote code execution. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2020-3992 to this issue. This patch contains the complete fix for CVE-2020-3992. For more information, see VMware Security Advisory VMSA-2020-0023.1.
Vmware Esxi Free Vs Paid
| Profile Name | ESXi-6.7.0-20201103001-standard |
| Build | For build information, see Patches Contained in this Release. |
| Vendor | VMware, Inc. |
| Release Date | November 4, 2020 |
| Acceptance Level | PartnerSupported |
| Affected Hardware | N/A |
| Affected Software | N/A |
| Affected VIBs |
|
| PRs Fixed | N/A |
| Related CVE numbers | CVE-2020-3992 |
This patch updates the following issue:
OpenSLP as used in ESXi has a use-after-free issue. This issue might allow a malicious actor with network access to port 427 on an ESXi host to trigger a use-after-free in the OpenSLP service resulting in remote code execution. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2020-3992 to this issue. This patch contains the complete fix for CVE-2020-3992. For more information, see VMware Security Advisory VMSA-2020-0023.1.
Vmware Esxi Free For Personal Use
| Profile Name | ESXi-6.7.0-20201103001-no-tools |
| Build | For build information, see Patches Contained in this Release. |
| Vendor | VMware, Inc. |
| Release Date | November 4, 2020 |
| Acceptance Level | PartnerSupported |
| Affected Hardware | N/A |
| Affected Software | N/A |
| Affected VIBs |
|
| PRs Fixed | N/A |
| Related CVE numbers | CVE-2020-3992 |
This patch updates the following issue:
OpenSLP as used in ESXi has a use-after-free issue. This issue might allow a malicious actor with network access to port 427 on an ESXi host to trigger a use-after-free in the OpenSLP service resulting in remote code execution. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2020-3992 to this issue. This patch contains the complete fix for CVE-2020-3992. For more information, see VMware Security Advisory VMSA-2020-0023.1.
